You can use the hard disk of your imageRUNNER ADVANCE machine to perform numerous convenient operations including copying, sending, and receiving data.
Even if the hard disk is removed from the machine, it is virtually impossible to analyze the data stored in the disk.
Data Security
The figure below shows a comparison of the hard disks of imageRUNNER ADVANCE machines and computers.
|
For Computers
 Hard disk
|
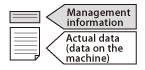 |
Data is separated for storage into 'Management Information', such as the file name, and 'Actual Data', the content of the data.
|
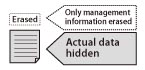 |
Operations that erase data (e.g. emptying the recycle bin, formatting, etc.) only erase 'Management Information'.
Actual data remains hidden in the hard disk.
|
|
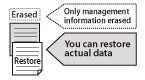 |
You can restore actual data hidden on the hard disk using file restoration software.
|
|
|
For imageRUNNER ADVANCE machines
Hard disk
|
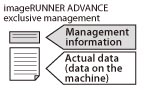 |
Data is separated for storage into 'Management Information', such as the file name, and 'Actual Data', the content of the data.
Management information is managed using a method exclusive to imageRUNNER ADVANCE machines.
|
 |
Management information is erased following copy, send/receive, and printing operations. However, actual data remains hidden in the hard disk.
|
|
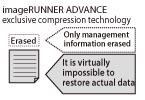 |
You cannot access actual data in the machine's hard disk from the machine's display or a computer on the network.
Also, removing and analyzing the machine's hard disk is made virtually impossible due to the need to analyze Canon confidential imageRUNNER ADVANCE firmware and data compression technology in the process.
|
Expanding the data erase function:
 |
 |
By using the data erase kit, you can completely erase all actual data.
This helps to strengthen an already robust security system.
* The Data Erase function performs processing in real-time, avoiding batch processing. This function also enables you to suppress job log data.
|
Initialize All Data/Settings
You can manually erase all user data stored in the machine when discarding or moving the machine.
This section describes how to initialize all data and settings contained in the machine's memory.
Initialize All Data/Settings
1.
Press  → [Management Settings] → [Data Management] → [Initialize All Data/Settings].
→ [Management Settings] → [Data Management] → [Initialize All Data/Settings].
 → [Management Settings] → [Data Management] → [Initialize All Data/Settings].
→ [Management Settings] → [Data Management] → [Initialize All Data/Settings].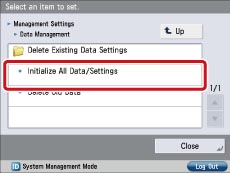
2.
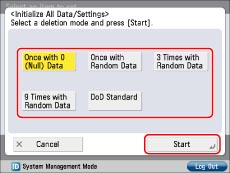
Select the deletion mode → press [Start].
|
[Once with 0 (Null) Data]:
|
Overwrite the data once with 0 (null) data.
|
|
[Once with Random Data]:
|
Overwrite the data once with random data.
|
|
[3 Times with Random Data]:
|
Overwrite the data three times with random data.
|
|
[9 Times with Random Data]:
|
Overwrite the data three times with random data.
|
|
[DoD Standard]:
|
Overwrite the data three times. The first time is with a fixed value, the second time with a complement of the fixed value, and the third time is with random data.
|
|
NOTE
|
|
It may take more than 30 minutes to initialize all the data and settings.
|
3.
After initialization is complete, the energy saver key automatically turns OFF and the main power switch of the machine automatically switches to OFF.
Reference Information
HDD Actual Data Encryption (Optional)
You can use HDD Data Encryption to automatically encrypt actual data when storing your electronic files in the hard disk using the Fax and other functions.
In addition, you can automatically erase all job data from the machine.
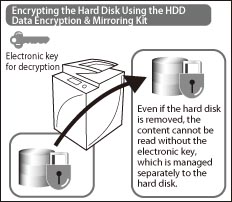
HDD All Data Encryption (Optional)
This function enables you to encrypt all data, including temporary data, at the time of writing.
Even if the hard disk is removed from the machine, data in the disk cannot be decoded without the electronic key, preventing the leakage of confidential information such as Address Book data.
HDD Actual Data Erase (Optional)
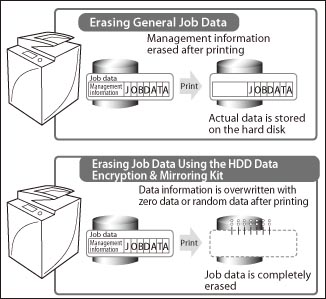
Your imageRUNNER ADVANCE machine separates data into management information and actual data before storing the data.
Management information is automatically erased when the copy, send/receive, or print operation is completed. However, actual data is stored and remains in the hard disk.
By using the data erase function, actual data (image, management, and spool data for the copying, printing, and sending/receiving functions) is erased at the same time as management information.
|
NOTE
|
|
Temporary job data that is created in the hard disk is automatically erased when the job completes.
An erase method can be selected according to a company's security policy from the following four options:
Once with 0 (Null) Data
Once with Random Data
3 Times with Random Data
DOD Standard
The above measures can help prevent the leakage of important information.
|