Restricting Access by Authentication
The authentication on this machine requests user information (user name and password) when users access the machine, and verifies that information. Only an authorized user that has successfully passed the authentication can operate the machine. You can prevent access by unauthorized users by managing the users for the machine. To use the authentication mode, you must first register the information for administrators and general users.
The administrator can restrict various functions such as Copy, Print, and Send that each user can use and limit the maximum number of copies/prints that each user can output. Also, if necessary, the administrator can restrict settings on "Settings/Registration."
Authentication Information (Administrator/General User/Unauthorized User)
The administrator manages the users by restricting access by general user and setting restrictions on operations using the authentication mode. General user privileges can be set per users. By preventing access by unauthorized users, administrators can reduce the threat of tampering of the machine and information leakage.
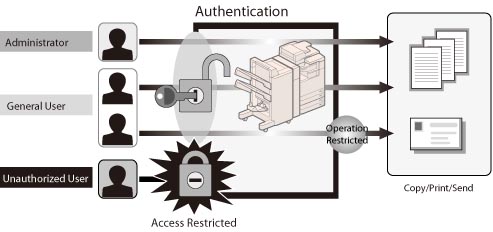
You can use the following authentication functions:
Department ID Management (Default Authentication)
You can manage the users by department or project by registering the Department ID and PIN. The Department ID Management enables you to restrict various functions such as Copy, Print, and Send that each department can use, and the Page Limits for Copy, Scan, and Print for each department. (See "Department ID Management.")
SSO-H (Single Sign-On H)
The SSO-H enables you to perform user authentication by registering user names and passwords.
There are two types of authentication method: Domain Authentication, which performs login authentication for the machine and authentication of the domain on the network in conjunction with the domain controller of the Active Directory, and Local Device Authentication, which performs authentication using only the machine. You can use both authentication methods at the same time. (See "SSO-H (Single Sign-On H).")
Also, you can limit use of particular device functions for each user using the ACCESS MANAGEMENT SYSTEM. (For information on the optional products required to use access management, see "Optional Products Required for Each Function.") For example, you can restrict Copy/Print functions, such as 2-sided printing, or the use of various settings in Settings/Registration.
User Setting Information Management (User Setting Information Management Service)
This mode enables you to link information such as the user name and password set for each function by each user with the SSO-H user information.
You can delete the user setting information that each user is using from the User Setting Information Management Service page. (See "User Setting Information Management (User Setting Information Management Service).")
User Access Control for Advanced Space
[User Access Control for Advanced Space] enables you to manage user authentication when the Advanced Space on the machine is used, or when the Advanced Space is opened externally on the network and is being used as a server. (See "User Access Control for Advanced Space.")