Configuring the IEEE 802.1X Authentication Settings
In a network environment that uses IEEE 802.1X authentication, unauthorized network access is blocked by a LAN switch (authenticator) that only grants access privileges to client devices (supplicants) that are authorized by the authentication server (RADIUS server). To connect this machine to an IEEE 802.1X network, settings such as the authentication method used by the authentication server must be configured on the machine. Administrator privileges are required in order to configure these settings.
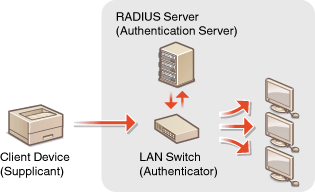
IEEE 802.1X Authentication Method
The machine supports the authentication methods described below. You must register a CA certificate before using any of these authentication methods. Registering a CA Certificate
 EAP-TLS (Extensible Authentication Protocol-Transport Level Security)
EAP-TLS (Extensible Authentication Protocol-Transport Level Security)
The machine and the authentication server authenticate each other by mutually sending certificates. A CA certificate must be registered on the machine to verify the certificate (server certificate) sent from the authentication server. In addition, a PKCS#12 format key and certificate (client certificate) must be specified in this setting, so that the authentication server can authenticate the machine. Register these items before configuring the settings (Registering a Key and Certificate). This authentication method cannot be used in combination with the other methods.
 EAP-TTLS (EAP-Tunneled TLS)
EAP-TTLS (EAP-Tunneled TLS)
Only the authentication server sends a certificate. A CA certificate must be registered on the machine to verify the certificate (server certificate) sent from the authentication server. In addition, a user name and password need to be specified in these settings, so that the authentication server can authenticate the machine. Microsoft Challenge Handshake Authentication Protocol Version 2 (MS-CHAPv2) or Password Authentication Protocol (PAP) can be selected as the internal authentication protocol to support EAP-TTLS.
 PEAP (Protected EAP)
PEAP (Protected EAP)
Only the authentication server sends a certificate. A CA certificate must be registered on the machine to verify the certificate (server certificate) sent from the authentication server. In addition, a user name and password need to be specified in these settings, so that the authentication server can authenticate the machine. Only MS-CHAPv2 can be selected as the internal authentication protocol to support PEAP.
Setting the IEEE 802.1X Authentication Method
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Network Settings]  [IEEE 802.1X Settings].
[IEEE 802.1X Settings].
 [IEEE 802.1X Settings].
[IEEE 802.1X Settings].4
Select [Use IEEE 802.1X] and configure the required settings.
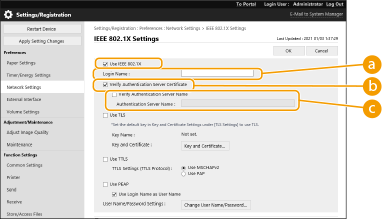
 [Login Name]
[Login Name]Enter the name (EAP Identity) of the login user to receive IEEE 802.1X authentication.
 [Verify Authentication Server Certificate]
[Verify Authentication Server Certificate]Select this check box when verifying server certificates sent from an authentication server.
 [Verify Authentication Server Name]
[Verify Authentication Server Name]To verify the common name in the server certificate, select this check box and enter the name of the authentication server where the login user is registered in [Authentication Server Name].
5
Select the authentication method and configure the necessary settings.
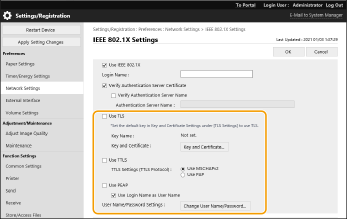
 Selecting EAP-TLS
Selecting EAP-TLS
1 | Select [Use TLS] and click [Key and Certificate]. |
2 | Click [Use] for the key to use in the list. |
 Selecting EAP-TTLS/PEAP
Selecting EAP-TTLS/PEAP
1 | Select [Use TTLS] or [Use PEAP]. To use EAP-TTLS, select [Use MSCHAPv2] or [Use PAP] for [TTLS Settings (TTLS Protocol)]. |
2 | Click [Change User Name/Password]. To set a user name that differs from the login name for IEEE 802.1X authentication, deselect [Use Login Name as User Name]. To use the same name as the login name for IEEE 802.1X authentication, leave it selected. |
3 | Enter the user name and password. To set or change the password, select this check box and enter the same password in [Password] and [Confirm]. |
6
Click [OK].
 |
Using the operation panelYou can also enable or disable IEEE 802.1X authentication from <Set> in the <Home> screen. <IEEE 802.1X Settings> Batch importing/batch exportingThis setting can be imported/exported with models that support batch importing of this setting. Importing/Exporting the Setting Data This setting is included in [Settings/Registration Basic Information] when batch exporting. Importing/Exporting All Settings |