Checking the Results of Monitoring Security Policies
This section describes the method for checking the results of monitoring security policies.
You can check the result of comparing with the standard security policy and the number of times that security policies have been overwritten for each printer.
NOTE |
The number of times that security policies have been overwritten cannot be retrieved from some models. In this case, the number is always zero. For details on the corresponding models, see the following. Types of Printer and Corresponding Printer Models (Displayed in a separate tab) |
Displaying the List of Successful Printers for Security Policy Monitoring
You can check the printers that security policy monitoring was successful for with a [Monitor/Distribute Security Policies] task.
1.
Select the [Devices] menu > [Security Data] > [Security Policies].
2.
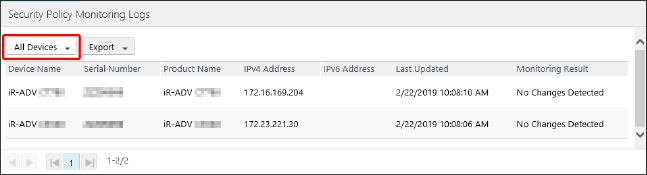
Perform the required operations in the list on the [Security Policy Monitoring Logs] page.
The monitoring result of each printer is displayed in the list.
When monitoring results that meet the following conditions are displayed multiple consecutive times, only the latest monitoring result is displayed.
When the security policy of the printer matches the standard and there is no problem with the policy change count
In the following cases, all the monitoring results are displayed.
When the security policy does not match the standard
When the security policy has been overwritten, even if it matches the standard
The display can be switched using the drop-down list on the top of the list, as required.
Exporting the monitoring history
Select the file format in the [Export] drop-down list on the top of the list.
Follow the instructions on the screen to save the file.
There are cautions to follow when exporting to a CSV file. For details, see the following.
Checking the Detailed Monitoring Result of Each Printer
1.
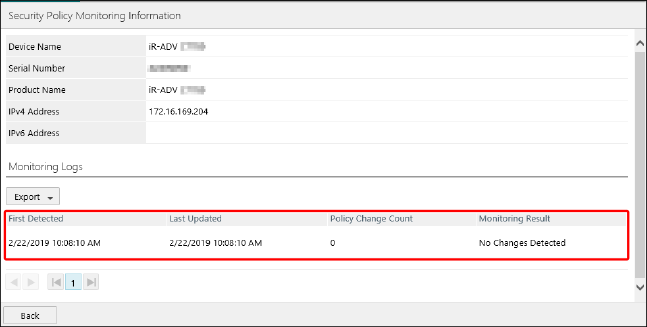
Select the desired printer from the list on the [Security Policy Monitoring Logs] page.
The monitoring history is displayed on the [Security Policy Monitoring Information] page.
IMPORTANT |
Regarding [Policy Change Count]Each time the security policy of a printer is overwritten with a [Monitor/Distribute Security Policies] task, the number of items included in the security policy is added to the policy change count. (Regardless of whether the settings are actually overwritten.) Therefore, even if only one item is overwritten, the policy change count will not be "1." |
Exporting the monitoring history
Select the file format in the [Export] drop-down list on the top of the [Monitoring Logs] list.
Follow the instructions on the screen to save the file.
There are cautions to follow when exporting to a CSV file. For details, see the following.
Checking the monitoring result of each item
Select the target history in the list.
On the [Security Policy Monitoring Log Details] page, you can check the result of comparing each item with the values of the standard security policy and the number of times that security policies have been overwritten.
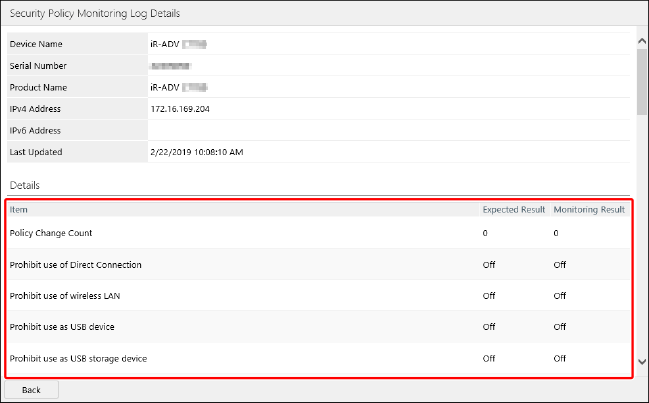
The background color of items that do not match the standard security policy is highlighted.