Generating the Key and Certificate for Network Communication
 | The machine can generate the key and certificate (server certificate) used for TLS encrypted communication. If you want to start using TLS encrypted communication immediately, it is convenient to use the key and certificate that are preinstalled in the machine. If necessary, have an administrator generate a key and certificate. Note, however, that TLS encrypted communication is not enabled simply by generating a key and certificate. Configuring the Key and Certificate for TLS |
 |
If you want to use a server certificate with a CA signature, you can generate the key along with a CSR, instead of the certificate. Generating a Key and CSR |
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Device Management]  [Key and Certificate Settings].
[Key and Certificate Settings].
 [Key and Certificate Settings].
[Key and Certificate Settings].4
Click [Generate Key].

Deleting a registered key and certificate
Select the key and certificate to delete → click [Delete]  [OK].
[OK].
 [OK].
[OK].A key and certificate cannot be deleted if it is currently used for some purpose, such as when "TLS" or "IEEE 802.1X" is displayed under [Key Usage]. In this case, disable the function or replace the other key and certificate before deleting it.
5
Click [Network Communication].
6
Specify settings for the key and certificate.
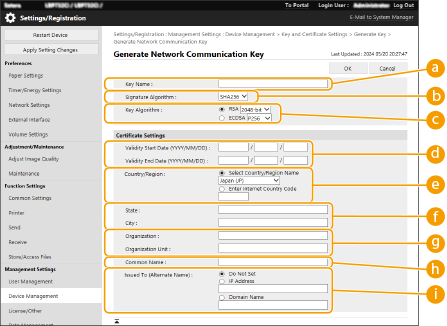
 [Key Name]
[Key Name]Enter alphanumeric characters for naming the key. Set a name that will be easy for you to find later in a list.
 [Signature Algorithm]
[Signature Algorithm]Select the hash algorithm to use for the signature. The available hash algorithms vary depending on the key length (Management Functions). A key length of 1024 bits or more can support SHA384 and SHA512 hash algorithms.
 [Key Algorithm]
[Key Algorithm]Select [RSA] or [ECDSA] as the key generation algorithm. Select the key length if you selected [RSA] and the key type if you selected [ECDSA]. In both cases, a higher value provides greater security but reduces the communication processing speed.

If [SHA384] or [SHA512] is selected for [Signature Algorithm], the key length cannot be set to [512-bit] when [RSA] is selected for [Key Algorithm].
 [Validity Start Date (YYYY/MM/DD)]/[Validity End Date (YYYY/MM/DD)]
[Validity Start Date (YYYY/MM/DD)]/[Validity End Date (YYYY/MM/DD)]Enter the start date and end date of the validity period for the certificate. [Validity End Date (YYYY/MM/DD)] cannot be set to a date before the date in [Validity Start Date (YYYY/MM/DD)].
 [Country/Region]
[Country/Region]Click the [Select Country/Region Name] radio button and select the country/region from the drop-down list. You can also click the [Enter Internet Country Code] radio button and enter a country code, such as "US" for the United States.
 [State]/[City]
[State]/[City]Enter alphanumeric characters for the location as necessary.
 [Organization]/[Organization Unit]
[Organization]/[Organization Unit]Enter alphanumeric characters for the organization name as necessary.
 [Common Name]
[Common Name]Enter alphanumeric characters for the common name of the certificate as necessary. "Common Name" is often abbreviated as "CN."
 [Issued To (Alternate Name)]
[Issued To (Alternate Name)]Enter the IP address or domain to be set for the Subject Alternative Name (SAN), as needed.
If you are not configuring the [Issued To (Alternate Name)] setting, select the [Do Not Set] checkbox.
Only IPv4 addresses can be set in [IP Address].
7
Click [OK].
Generating a key and certificate may take some time.
After the key and certificate is generated, it is automatically registered to the machine.