
Security and Management Function Specifications (imageRUNNER 2224N II)
Firewall Settings
When specifying IP addresses in firewall settings, up to 16 IP addresses (or ranges of IP addresses) can be specified for both IPv4 and IPv6.
When specifying MAC addresses in firewall settings, up to 32 MAC addresses can be specified.
Registration of Certificates (User Signature Keys/Certificates, CA Certificates, S/MIME Certificates)
The algorithms and formats of keys and certificates that can be registered are as follows.
RSA signature algorithm: | SHA-1*2/SHA-256/SHA-384*1/SHA-512*1 |
RSA public-key algorithm (key length): | RSA (512 bits/1024 bits/2048 bits/4096 bits) |
DSA signature algorithm: | SHA-1*2 |
DSA public-key algorithm (key length): | DSA (1024 bits/2048 bits/3072 bits) |
ECDSA signature algorithm: | SHA-1*2/SHA-256/SHA-384/SHA-512 |
ECDSA public-key algorithm (key length): | ECDSA (P256/P384/P521) |
Certificate format: | User Signature Keys/Certificates: PKCS#12 CA Certificates, S/MIME Certificates: X.509 DER/PEM |
File extension: | User Signature Keys/Certificates: p12/pfx CA Certificates, S/MIME Certificates: cer/pem |
Maximum number of registerable certificates: | Keys, Certificates: 5 CA Certificates: 88 |
*1 Available only when the key algorithm is 1024 bits or more. *2 Available only when installed by using the Remote UI. | |
Definition of "Weak Encryption"
When [Prohibit Use of Weak Encryption] in [Encryption Settings] is set to [On], the use of the following algorithms is prohibited. [Encryption Settings]
Hash: | MD4, MD5, SHA-1 |
HMAC: | HMAC-MD5 |
Common key cryptosystem: | RC2, RC4, DES |
Public key cryptosystem: | RSA encryption (512 bits/1024 bits), RSA signature (512 bits/1024 bits), DSA (512 bits/1024 bits), DH (512 bits/1024 bits) |
 |
Even when [Prohibit Key/Cert. with Weak Encryption] in [Encryption Settings] is set to [On], the hash algorithm SHA-1, which is used for signing a root certificate, can be used. |
Log Type
You can manage the following logs on the machine. The recorded logs can be sent to an SIEM (security information/event management) system via the Syslog protocol.
Log Type | Number Indicated as "Log Type" | Description |
User Authentication Log | 4098 | This log contains information related to the authentication status of user authentication (login/logout and user authentication success/failure), the registering/changing/deleting of user information managed with User Authentication. |
Job Log | 1001 | This log contains information related to the completion of copy/scan/send/print jobs. |
Transmission Log | 8193 | The log contains information related to transmissions. |
Machine Management Log | 8198 | This log contains information related to the starting/shutting down of the machine, changes made to the settings by using the [Menu]. The Machine Management Log also records changes in user information or security-related settings when the machine is inspected or repaired by your dealer or service representative. |
Network Authentication Log | 8200 | This log is recorded when IPSec communication fails. |
Export/Import All Log | 8202 | This log contains information related to the importing/exporting of the settings by using the Export All/Import All function. |
Security Policy Log | 8204 | This log contains information related to the setting status of the security policy settings. |
System Maintenance Log | 8206 | This log contains information related to firmware updates and backup/restoration of the MEAP application, etc. |
Import/Export of the Setting Data
Max. Destinations Registered to Address Book
TLS
The following combinations of the TLS version and algorithm are usable:
 : Usable
: Usable 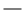 : Not usable
: Not usableAlgorithm | TLS Version | |||
TLS 1.3 | TLS 1.2 | TLS 1.1 | TLS 1.0 | |
Encryption Algorithm | ||||
AES-CBC (256bit) | 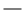 |  |  |  |
AES-CBC (128bit) | 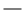 |  |  |  |
AES-GCM (256bit) |  |  | 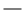 | 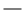 |
AES-GCM (128bit) |  |  | 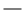 | 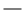 |
3DES-CBC | 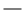 |  |  |  |
CHACHA20-POLY1305 |  | 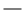 | 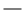 | 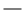 |
Key Exchange Algorithm | ||||
RSA | 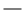 |  |  |  |
ECDHE |  |  |  |  |
X25519 |  | 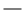 | 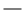 | 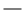 |
Signature Algorithm | ||||
RSA |  |  |  |  |
ECDSA |  |  |  |  |
HMAC Algorithm | ||||
SHA1 | 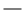 |  |  |  |
SHA256 |  |  | 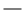 | 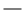 |
SHA384 |  |  | 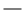 | 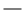 |