Configuring IPSec Settings
Internet Protocol Security (IPSec or IPsec) is a protocol suite for encrypting data transported over a network, including Internet networks. While TLS only encrypts data used on a specific application, such as a Web browser or an e-mail application, IPSec encrypts either whole IP packets or the payloads of IP packets, offering a more versatile security system. The IPSec of the machine works in transport mode, in which the payloads of IP packets are encrypted. With this feature, the machine can connect directly to a computer that is in the same virtual private network (VPN). Check the system requirements and set the necessary configuration on the computer before you configure the machine.
System Requirements
IPSec that is supported by the machine conforms to RFC4301, RFC4302, RFC4303, and RFC4305.
|
Operating systems supported by communication partners
|
Windows Vista/7/8/10/Server 2008/Server 2012
|
|
|
Connection mode
|
Transport mode
|
|
|
Key exchange protocol
|
IKEv1
|
|
|
Print Mode
|
Main mode
Aggressive mode
|
|
|
Authentication method
|
Pre-shared key
Digital signature
|
|
|
Hash algorithm
|
HMAC-MD5-96
HMAC-SHA1-96
|
|
|
Encryption algorithm
(and key length) |
3DES-CBC
AES-CBC (128 bits, 192 bits, or 256 bits)
|
|
|
Key exchange algorithm/group (and key length)
|
Diffie-Hellman (DH)
Group 1 (768 bits)
Group 2 (1024 bits)
Group 14 (2048 bits)
|
|
|
ESP (Encapsulating Security Payload)
|
Hash algorithm
|
HMAC-MD5-96
HMAC-SHA1-96
|
|
Encryption algorithm
(and key length) |
3DES-CBC
AES-CBC (128 bits, 192 bits, or 256 bits)
|
|
|
AH (Authentication Header)
|
Hash algorithm
|
HMAC-MD5-96
HMAC-SHA1-96
|
 |
Before configuring IPSec communication settingsCheck the IPSec settings in the operating system the machine will communicate with. An incorrect combination of the operating system settings and machine settings will disable the IPSec communication.
|
 |
IPSec functional restrictionsIPSec supports communication to a unicast address (or a single device).
The machine cannot use both IPSec and DHCPv6 at the same time.
IPSec is unavailable in networks in which NAT or IP masquerade is implemented.
In IKEv1 phase1, PFS is not supported.
Using IPSec with IP address filterThe IPSec settings are applied before the IP address filter settings during packet reception while the IP address settings are applied before the IPSec settings during packet transmission. Specifying IP Addresses for Firewall Rules
|
Registering Security Policies
To use IPSec for encrypted communication, you need to register security policies (SP) before enabling the IPSec settings (Enabling IPSec Communication). A security policy consists of the groups of settings described below. Up to 10 policies can be registered. You can register multiple policies according to a combination of the IP address and the port number. After registering policies, specify the order in which they are applied.
Selector
Selector defines conditions for IP packets to apply IPSec communication. Selectable conditions include IP addresses and port numbers of the machine and the devices to communicate with.
IKE
IKE configures the IKEv1 that is used for key exchange protocol. Note that instructions vary depending on the authentication method selected.
[Pre-Shared Key Method]
A key of up to 24 alphanumeric characters can be shared with the other devices. Enable TLS for the Remote UI in advance (Using TLS for Encrypted Communications).
A key of up to 24 alphanumeric characters can be shared with the other devices. Enable TLS for the Remote UI in advance (Using TLS for Encrypted Communications).
[Digital Signature Method]
The machine and the other devices authenticate each other by mutually verifying their digital signatures. Have a key pair to use ready (Using CA-issued Key Pairs and Digital Certificates).
The machine and the other devices authenticate each other by mutually verifying their digital signatures. Have a key pair to use ready (Using CA-issued Key Pairs and Digital Certificates).
Setting Protocols and Options
Specify the settings for ESP and AH, which are added to packets during IPSec communication. ESP and AH cannot be used at the same time. You can also select whether or not to enable PFS for tighter security.
1
Start the Remote UI and log on in Management Mode. Starting Remote UI
2
Click [Settings/Registration].
3
Click [Security]  [IPSec Settings].
[IPSec Settings].
 [IPSec Settings].
[IPSec Settings].
4
Click [IPSec Policy List].
5
Click [Register IPSec Policy].
6
Enter a policy name in [Policy Name], and select the [Enable Policy] check box.
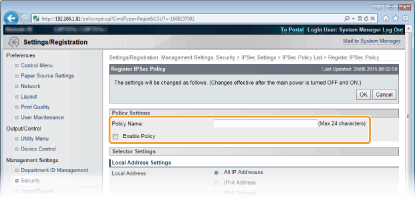
[Policy Name]
Enter up to 24 alphanumeric characters for a name that is used for identifying the policy.
Enter up to 24 alphanumeric characters for a name that is used for identifying the policy.
[Enable Policy]
Select the check box to enable the policy. When not using the policy, clear the check box.
Select the check box to enable the policy. When not using the policy, clear the check box.
7
Specify the selector settings.
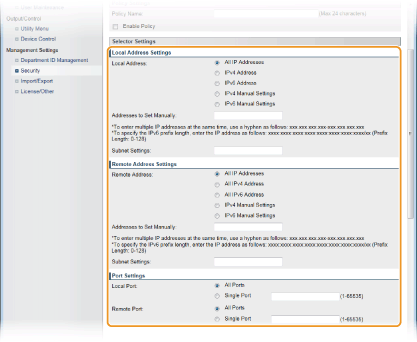
[Local Address]
Select the type of the IP address of the machine to apply the policy from the following list.
Select the type of the IP address of the machine to apply the policy from the following list.
|
[All IP Addresses]
|
Select to use IPSec for all IP packets.
|
|
[IPv4 Address]
|
Select to use IPSec for all IP packets that are sent to or from the IPv4 address of the machine.
|
|
[IPv6 Address]
|
Select to use IPSec for all IP packets that are sent to or from an IPv6 address of the machine.
|
|
[IPv4 Manual Settings]
|
Select to specify a single IPv4 address or a range of IPv4 addresses to apply IPSec. Enter the IPv4 address (or the range) in the [Addresses to Set Manually] text box.
|
|
[IPv6 Manual Settings]
|
Select to specify a single IPv6 address or a range of IPv6 addresses to apply IPSec. Enter the IPv6 address (or the range) in the [Addresses to Set Manually] text box.
|
[Addresses to Set Manually]
If [IPv4 Manual Settings] or [IPv6 Manual Settings] is selected for [Local Address], enter the IP address to apply the policy.
If [IPv4 Manual Settings] or [IPv6 Manual Settings] is selected for [Local Address], enter the IP address to apply the policy.
[Subnet Settings]
When manually specifying IPv4 addresses, you can express the range by using the subnet mask. Enter the subnet mask using periods to delimit numbers (example:"255.255.255.240").
When manually specifying IPv4 addresses, you can express the range by using the subnet mask. Enter the subnet mask using periods to delimit numbers (example:"255.255.255.240").
[Remote Address]
Select the type of IP address of the other devices to apply the policy from the list shown below.
Select the type of IP address of the other devices to apply the policy from the list shown below.
|
[All IP Addresses]
|
Select to use IPSec for all IP packets.
|
|
[All IPv4 Address]
|
Select to use IPSec for all IP packets that are sent to or from an IPv4 address.
|
|
[All IPv6 Address]
|
Select to use IPSec for all IP packets that are sent to or from an IPv6 address.
|
|
[IPv4 Manual Settings]
|
Select to specify a single IPv4 address or a range of IPv4 addresses to apply IPSec. Enter the IPv4 address (or the range) in the [Addresses to Set Manually] text box.
|
|
[IPv6 Manual Settings]
|
Select to specify a single IPv6 address or a range of IPv6 addresses to apply IPSec. Enter the IPv6 address (or the range) in the [Addresses to Set Manually] text box.
|
[Addresses to Set Manually]
If [IPv4 Manual Settings] or [IPv6 Manual Settings] is selected for [Remote Address], enter the IP address to apply the policy.
If [IPv4 Manual Settings] or [IPv6 Manual Settings] is selected for [Remote Address], enter the IP address to apply the policy.
[Subnet Settings]
When manually specifying IPv4 addresses, you can express the range by using the subnet mask. Enter the subnet mask using periods to delimit numbers (example:"255.255.255.240").
When manually specifying IPv4 addresses, you can express the range by using the subnet mask. Enter the subnet mask using periods to delimit numbers (example:"255.255.255.240").
[Local Port]/[Remote Port]
If you want to create separate policies for each protocol, such as HTTP or SMTP, enter the appropriate port number for the protocol to determine whether to use IPSec.
If you want to create separate policies for each protocol, such as HTTP or SMTP, enter the appropriate port number for the protocol to determine whether to use IPSec.

IPSec is not applied to the packets that have a specified multicast or broadcast address.
8
Specify the IKE Settings.
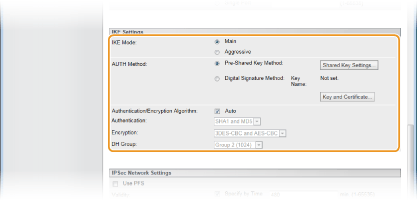
[IKE Mode]
The mode used for the key exchange protocol is displayed. Normally select the main mode.

Select the aggressive mode when the IP address is not fixed. Note that security is lower in the aggressive mode than in the main mode.
[AUTH Method]
Select [Pre-Shared Key Method] or [Digital Signature Method] for the method used when authenticating the machine.
Select [Pre-Shared Key Method] or [Digital Signature Method] for the method used when authenticating the machine.

When the aggressive mode is selected in [IKE Mode], the [Pre-Shared Key Method] setting does not encrypt the shared key.
[Authentication/Encryption Algorithm]
To automatically set the algorithm that is used for key exchange, select the [Auto] check box. If you select the check box, the algorithm is set as shown below.
To automatically set the algorithm that is used for key exchange, select the [Auto] check box. If you select the check box, the algorithm is set as shown below.
|
[Authentication]
|
[SHA1 and MD5]
|
|
[Encryption]
|
[3DES-CBC and AES-CBC]
|
|
[DH Group]
|
[Group 2 (1024)]
|
To manually set the algorithm, clear the check box and select the algorithm.
|
[Authentication]
|
Select the hash algorithm.
|
|
[Encryption]
|
Select the encryption algorithm.
|
|
[DH Group]
|
Select the Diffie-Hellman group, which determines the key strength.
|
 Using [Pre-Shared Key Method] for authentication
Using [Pre-Shared Key Method] for authentication
|
1
|
Select [Pre-Shared Key Method] for [AUTH Method] and click [Shared Key Settings].
|
|
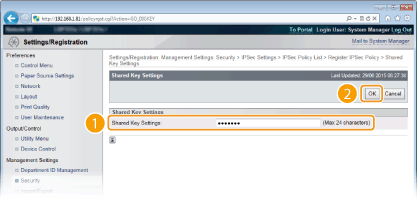
2
|
Enter up to 24 alphanumeric characters for the pre-shared key and click [OK].
 |
 Using [Digital Signature Method] for authentication
Using [Digital Signature Method] for authentication
|
1
|
Select [Digital Signature Method] for [AUTH Method] and click [Key and Certificate].
|
|
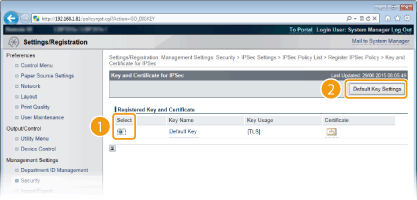
2
|
Select the key pair you want to use, and click [Default Key Settings].
  Viewing details of a key pair or certificate
You can check the details of the certificate or verify the certificate by clicking the corresponding text link under [Key Name], or the certificate icon. Verifying Key Pairs and Digital Certificates
|
9
Specify the IPSec Network Settings.
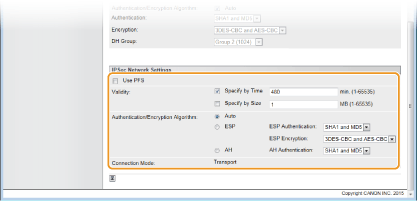
[Use PFS]
Select the check box to enable Perfect Forward Secrecy (PFS) for IPSec session keys. Enabling PFS enhances the security while increasing the load on the communication. Make sure that PFS is also enabled for the other devices. When not using PFS, clear the check box.
[Validity]
Specify how long SA is used as a communication tunnel. Select the [Specify by Time] or [Specify by Size] check box or both check boxes as necessary. If both check boxes are selected, the IPSec SA session is terminated when either of the conditions has been satisfied.
Specify how long SA is used as a communication tunnel. Select the [Specify by Time] or [Specify by Size] check box or both check boxes as necessary. If both check boxes are selected, the IPSec SA session is terminated when either of the conditions has been satisfied.
|
[Specify by Time]
|
Enter a time in minutes to specify how long a session lasts. The entered time is applied to both IPSec SA and IKE SA.
|
|
[Specify by Size]
|
Enter a size in megabytes to specify how much data can be transported in a session. The entered size is applied to IPSec SA only.
|

If you have selected the [Specify by Size] check box only
The IKE SA validity cannot be specified by size, so that the initial value (480 minutes) of [Specify by Time] is applied.
[Authentication/Encryption Algorithm]
Select the protocol and algorithm to use for IPSec communication.
Select the protocol and algorithm to use for IPSec communication.
 Automatically setting up connection
Automatically setting up connectionSelect [Auto].
|
[ESP Authentication]
|
ESP is enabled and the authentication algorithm is set to [SHA1 and MD5].
|
|
[ESP Encryption]
|
ESP is enabled and the encryption algorithm is set to [3DES-CBC and AES-CBC].
|
 Using ESP
Using ESPChoose [ESP] and select the authentication algorithm and encryption algorithm.
|
[ESP Authentication]
|
Select the hash algorithm to use for ESP authentication.
|
|
[ESP Encryption]
|
Select the encryption algorithm for ESP.
|
 Using AH
Using AHChoose [AH], and select the hash algorithm to use for AH authentication from [AH Authentication].
[Connection Mode]
The connection mode of IPSec is displayed. The machine supports transport mode, in which the payloads of IP packets are encrypted. Tunnel mode, in which whole IP packets (headers and payloads) are encapsulated is not available.
The connection mode of IPSec is displayed. The machine supports transport mode, in which the payloads of IP packets are encrypted. Tunnel mode, in which whole IP packets (headers and payloads) are encapsulated is not available.
10
Click [OK].
If you need to register an additional security policy, return to step 5.
11
Arrange the order of policies listed under [IPSec Policy List].
Policies are applied from one at the highest position to the lowest. Click [Raise Priority] or [Lower Priority] to move a policy up or down the order.
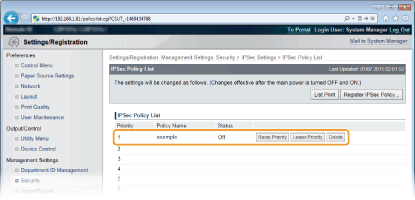

Editing a policy
You can click the text link under [Policy Name] to edit the settings.
Deleting a policy
Click [Delete] on the right of the policy that you want to delete.
12
Perform a hard reset.
Click [Device Control], select [Hard Reset], and then click [Execute].
The settings are enabled after a hard reset is performed.
Enabling IPSec Communication
After completion of registering security policies, enable the IPSec communication.
1
Start the Remote UI and log on in Management Mode. Starting Remote UI
2
Click [Settings/Registration].

3
Click [Security]  [IPSec Settings].
[IPSec Settings].
 [IPSec Settings].
[IPSec Settings].
4
Click [Edit].
5
Select the [Use IPSec] check box and click [OK].
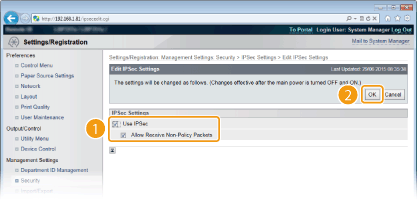
[Use IPSec]
When using IPSec in the machine, select the check box. When not using, clear the check box.
[Allow Receive Non-Policy Packets]
If you select the check box when using IPSec, packets that are not available for the registered policies are also sent/received. To disable sending/receiving the packets that are not available for the policies, clear the check box.
If you select the check box when using IPSec, packets that are not available for the registered policies are also sent/received. To disable sending/receiving the packets that are not available for the policies, clear the check box.
6
Perform a hard reset.
Click [Device Control], select [Hard Reset], and then click [Execute].

The settings are enabled after the hard reset is performed.
 |
Using the operation panelYou can also enable or disable IPSec communication from the setting menu of the operation panel. IPSec
|