Configuring the Network Security Settings
Authorized users may incur unanticipated losses from attacks by malicious third parties, such as sniffing, spoofing, and tampering of data as it flows over a network. To protect your important and valuable information from these attacks, the machine supports the following features to enhance security and secrecy.
Firewall Settings
Unauthorized access by third parties, as well as network attacks and intrusions, can be blocked by limiting communication only to devices that have a specific IP address or MAC address. Restricting Communication by Using Firewalls

Changing Port Numbers
A protocol that is used to exchange information with other devices is assigned port numbers that are predetermined according to the type of protocol. The port number must be the same for all communication devices; therefore, changing it to an arbitrary number is important to prevent hacking from outside. Changing Port Numbers
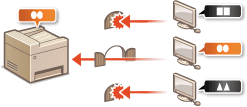
Proxy Settings
When the client devices are connected to an external network, communication is established through the proxy server. When the proxy server is used, websites can be browsed more safely, therefore, security can be expected to be enhanced. Setting a Proxy

TLS Encrypted Communication
TLS is a protocol for encryption for data sent over a network and is often used for communication via a Web browser or an e-mail application. TLS enables secure network communication when you access the machine from a computer via the Remote UI. Configuring the Key and Certificate for TLS
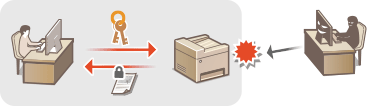
IEEE 802.1X Authentication
IEEE 802.1X is a standard and mechanism for blocking unauthorized access to the network by collectively managing user authentication information. If a device tries to connect to the 802.1X network, the device must go through user authentication in order to prove that the connection is made by an authorized user.
Authentication information is sent to and checked by a RADIUS server, which permits or rejects communication to the network depending on the authentication result. If authentication fails, a LAN switch (or an access point) blocks access from the outside of the network. The machine can connect to an 802.1X network as a client device. Configuring IEEE 802.1X Authentication Settings
Authentication information is sent to and checked by a RADIUS server, which permits or rejects communication to the network depending on the authentication result. If authentication fails, a LAN switch (or an access point) blocks access from the outside of the network. The machine can connect to an 802.1X network as a client device. Configuring IEEE 802.1X Authentication Settings
