
Configuring the Expiration Check Method for Received Certificates
There are two methods for verifying whether certificates received from the other party in communication are valid: Comparing with the certificate revocation list (CRL) registered in the machine and querying an OCSP (online certificate status protocol) responder (a server that supports OCSP). Set the method for checking the expiration of certificates according to your environment. This registration can only be performed by the administrator.
Registering a Certificate Revocation List (CRL)
You can use the Remote UI to register a certificate revocation list (CRL). For information on the CRLs that can be registered on the machine, see Management Functions.
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Device Management]  [Certificate Revocation List (CRL) Settings].
[Certificate Revocation List (CRL) Settings].
 [Certificate Revocation List (CRL) Settings].
[Certificate Revocation List (CRL) Settings].4
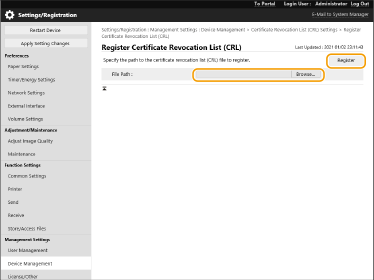
Click [Register CRL].
5
Register the CRL.
Click [Browse...], specify the file (CRL) to register, and click [Register].
 |
Managing CRLsYou can check the detailed settings or delete CRLs on the screen displayed in step 4. Click To delete a CRL, select the one that you want to delete, and click [Delete]  [OK]. [OK].Batch importing/batch exportingThis setting can be imported/exported with models that support batch importing of this setting. Importing/Exporting the Setting Data This setting is included in [Certificate/Certificate Revocation List (CRL) Settings] when batch exporting. Importing/Exporting All Settings |
Configuring the Online Certificate Status Protocol (OCSP)
You can configure the certificate verification level and the OCSP responder to connect to.
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Device Management]  [OCSP (Online Certificate Status Protocol) Settings].
[OCSP (Online Certificate Status Protocol) Settings].
 [OCSP (Online Certificate Status Protocol) Settings].
[OCSP (Online Certificate Status Protocol) Settings].4
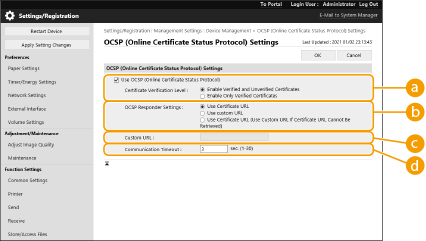
Select the check box for [Use OCSP (Online Certificate Status Protocol)], and configure the online certificate status protocol (OCSP).
 [Certificate Verification Level]
[Certificate Verification Level]Set whether to disable certificates in situations such as the following:
When the machine cannot connect to the OCSP responder
When a timeout occurs
When expiration cannot be checked, such as when the result of checking the expiration of a certificate via the OCSP responder is unknown
 [OCSP Responder Settings]
[OCSP Responder Settings]Specify the URL for connecting to the OCSP responder.
 [Custom URL]
[Custom URL]When [Use custom URL] or [Use Certificate URL (Use Custom URL If Certificate URL Cannot Be Retrieved)] is selected, enter the URL of the OCSP responder (ASCII code only, maximum 255 characters).
 [Communication Timeout]
[Communication Timeout]Set the time until communication with the OCSP responder times out. The connection is canceled if there is no response from the OCSP responder within the set time.
5
Click [OK].
 |
Batch importing/batch exportingThis setting can be imported/exported with models that support batch importing of this setting. Importing/Exporting the Setting Data This setting is included in [Settings/Registration Basic Information] when batch exporting. Importing/Exporting All Settings |