
<Security Settings>
All the settings associated with the authentication function and encryption are listed with descriptions. Default Settings are marked with a dagger  .
.
 .
. Asterisks (*) |
Settings marked with an asterisk (*) cannot be imported or exported. |
<Authentication/Password Settings> *
You can reinforce the security of the authentication function.
<Authentication Function Settings>
Configure the security functions for user authentication.
<Lockout>
When a user has failed user authentication, specify whether to disable the user from temporarily logging in to the machine (lockout). When <On> is selected, specify how many consecutive times failures are permitted before lockout is activated and also the time required before a user can log in again after lockout.
<Enable Lockout> <Off>  <On> <Lockout Threshold> 1  to 10 (time(s)) to 10 (time(s))<Lockout Period> 1 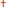 to 60 (min.) to 60 (min.) |
<Menu>  <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Authentication/Password Settings>
<Authentication/Password Settings>  <Authentication Function Settings>
<Authentication Function Settings>  <Lockout>
<Lockout>  Select <On> in <Enable Lockout>
Select <On> in <Enable Lockout>  Specify each setting item
Specify each setting item  <Apply>
<Apply>  Restart the machine
Restart the machine
 <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Authentication/Password Settings>
<Authentication/Password Settings>  <Authentication Function Settings>
<Authentication Function Settings>  <Lockout>
<Lockout>  Select <On> in <Enable Lockout>
Select <On> in <Enable Lockout>  Specify each setting item
Specify each setting item  <Apply>
<Apply>  Restart the machine
Restart the machine
This option is not applied to login using the department ID.
<Encryption Settings> *
Configure a setting for disabling a weak encryption or the key and certification using a weak encryption.
<Prohibit Use of Weak Encrypt.> <Off> 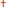 <On> <Prohibit Weak Encryp. Key/Cert.> <Off> 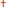 <On> |
<Menu>  <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Encryption Settings>
<Encryption Settings>  Select <On> in <Prohibit Use of Weak Encrypt.>
Select <On> in <Prohibit Use of Weak Encrypt.>  Select <Off> or <On> in <Prohibit Weak Encryp. Key/Cert.>
Select <Off> or <On> in <Prohibit Weak Encryp. Key/Cert.>  <Apply>
<Apply>  Restart the machine
Restart the machine
 <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Encryption Settings>
<Encryption Settings>  Select <On> in <Prohibit Use of Weak Encrypt.>
Select <On> in <Prohibit Use of Weak Encrypt.>  Select <Off> or <On> in <Prohibit Weak Encryp. Key/Cert.>
Select <Off> or <On> in <Prohibit Weak Encryp. Key/Cert.>  <Apply>
<Apply>  Restart the machine
Restart the machine<Verify System at Startup> 
When the machine starts or when an application (in Application Library) is executed, verification is performed to determine that the system or application has not been tampered. If tampering is detected, the machine enters a state to wait for firmware update. In this case, perform a firmware update operation from a computer. Updating the Firmware
<Off> 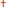 <On> |
<Menu>  <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Verify System at Startup>
<Verify System at Startup>  <On>
<On>  <Yes>
<Yes>  Restart the machine automatically
Restart the machine automatically
 <Management Settings>
<Management Settings>  <Security Settings>
<Security Settings>  <Verify System at Startup>
<Verify System at Startup>  <On>
<On>  <Yes>
<Yes>  Restart the machine automatically
Restart the machine automatically |
If nothing is displayed even after a while, system recovery may be impossible. In this case, contact your dealer or service representative. If an application installed after shipping of the machine from the factory has been tampered, it needs to be reinstalled on the machine. |