
Registering a Key and Certificate for Network Communication
You can use the Remote UI to register keys/certificates and CA certificates to the machine from your computer. Designate an administrator to register these items.

 |
The communication methods listed below use a key/certificate or CA certificate. If you want to use a registered key and certificate in actual communication, you need to specify the key and certificate in the settings for each communication method. However, an X.509 DER format CA certificate does not need to be specified in the settings for each communication method. You can use it simply by registering it to the machine. TLS encrypted communication Configuring the Key and Certificate for TLS |
Registering a Key and Certificate
Keys and certificates (server certificates) can be registered via the Remote UI. For information on the keys and certificates that can be registered on the machine, see Management Functions.
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Device Management]  [Key and Certificate Settings].
[Key and Certificate Settings].
 [Key and Certificate Settings].
[Key and Certificate Settings].4
Click [Register Key and Certificate].
5
Click [Install].
6
Install the key and certificate.
Click [Browse...], specify the files (key and certificate) to install, and click [Start Installation].
7
Register the key and certificate.
1 | Select the key and certificate that you want to register, and click [Register]. |
2 | Enter the key name and password, and click [OK]. 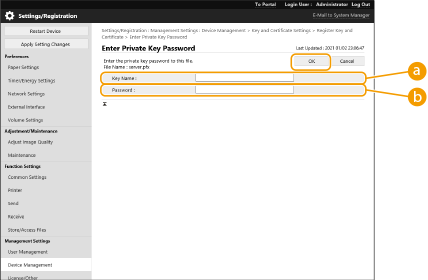  [Key Name] [Key Name]Use alphanumeric characters to enter the name of the key that was registered to the machine.  [Password] [Password]Use alphanumeric characters to enter the password of the private key that is set for the file to register. |
 |
Managing keys and certificatesYou can check the detailed settings or delete keys and certificates on the screen displayed in step 4. If If Click a key name to display detailed information about the certificate. You can also click [Verify Certificate] on this screen to check whether the certificate is valid. To delete a key and certificate, select the one that you want to delete, and click [Delete]  [OK]. [OK]. |
Registering a CA Certificate
X.509 DER format CA certificates are preinstalled in the machine. You can register a new CA certificate if it is required by a particular function. For information on the CA certificates that can be registered on the machine, see Management Functions.
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Device Management]  [CA Certificate Settings].
[CA Certificate Settings].
 [CA Certificate Settings].
[CA Certificate Settings].4
Click [Register CA Certificate].
5
Click [Install].
6
Install the CA certificate.
Click [Browse...], specify the file (CA certificate) to install, and click [Start Installation].
7
Register the CA certificate.
Select the CA certificate that you want to register, and click [Register].
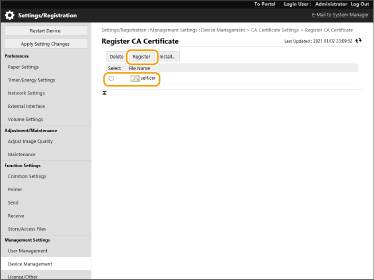
 |
Managing CA certificatesYou can check the detailed settings or delete CA certificates on the screen displayed in step 4. Click To delete a CA certificate, select the one that you want to delete, and click [Delete]  [OK]. [OK]. |