
Security and Management Function Specifications
Firewall
Up to 16 IP addresses (or ranges of IP addresses) can be specified for both IPv4 and IPv6.
Up to 32 MAC addresses can be specified.
IPSec
IPSec of the machine conforms to RFC2401, RFC2402, RFC2406, and RFC4305.
Operating system of connected device | Windows 8.1 Windows 10 Windows 11 |
Connection mode | Transport mode |
Key exchange protocol | IKEv1 (main mode) |
Authentication method Pre-shared key Digital signature | |
Hash algorithm (and key length) HMAC-SHA1-96 HMAC-SHA2 (256 bits or 384 bits) | |
Encryption algorithm (and key length) 3DES-CBC AES-CBC (128 bits, 192 bits, 256 bits) | |
Key exchange algorithm/group (and key length) Diffie-Hellman (DH) Group 14 (2048 bits) ECDH-P256 (256 bits) ECDH-P384 (384 bits) | |
ESP | Hash algorithm HMAC-SHA1-96 |
Encryption algorithm (and key length) 3DES-CBC AES-CBC (128 bits, 192 bits, 256 bits) | |
Hash/encryption algorithm (and key length) AES-GCM (128 bits, 192 bits, 256 bits) | |
AH | Hash algorithm HMAC-SHA1-96 |
 |
IPSec supports communication to a unicast address (single device). |
Keys and Certificates
The following keys and certificates are supported:
Self-generated Key and Self-signed Certificate or CSR
Public key algorithm (and key length) | RSA (512 bits, 1024 bits, 2048 bits, 4096 bits) DSA (1024Bits, 2048Bits, 3072Bits) ECDSA (P256, P384, P521) |
Certificate signature algorithm | RSA: SHA-1*1, SHA-256, SHA-384*2, SHA-512*2 DSA: SHA-1*1 ECDSA: SHA-1*1, SHA-256, SHA-384, SHA-512 |
Certificate thumbprint algorithm | SHA1 |
*1 Available only when installed by using the Remote UI.
*2 SHA384-RSA and SHA512-RSA are available only when the RSA key length is 1024 bits or more.
Key and Certificate or CA Certificate for Installation
Format | Key PKCS#12*1 CA certificate X.509 DER format/PEM format |
File extension | Key ".p12" or ".pfx" CA certificate ".cer" or ".pem" |
Public key algorithm (and key length) | RSA (512 bits, 1024 bits, 2048 bits, 4096 bits) DSA (1024 bits, 2048 bits, 3072 bits) ECDSA (P256, P384, P521) |
Certificate signature algorithm | RSA: SHA-1*2, SHA-256, SHA-384*3, SHA-512*3 DSA: SHA-1*2 ECDSA: SHA-1*2, SHA-256, SHA-384, SHA-512 |
Certificate thumbprint algorithm | SHA1 |
*1 Requirements for the certificate contained in a key are pursuant to CA certificates.
*2 Available only when installed by using the Remote UI.
*3 SHA384-RSA and SHA512-RSA are available only when the RSA key length is 1024 bits or more.
 |
The machine does not support use of a certificate revocation list (CRL). |
Definition of "Weak Encryption"
When [Prohibit Use of Weak Encrypt.] or [Prohibit Use of Weak Encryption] in [Encryption Settings] is set to [On], the use of the following algorithms is prohibited. [Encryption Settings]
Hash | MD4, MD5, SHA-1 |
HMAC | HMAC-MD5 |
Common key encryption | RC2, RC4, DES |
Public key encryption | RSA encryption (512 bits/1024 bits) RSA signature (512 bits/1024 bits) DSA (512 bits/1024 bits) DH (512 bits/1024 bits) |
 |
Even when [Prohibit Weak Encryp. Key/Cert.] or [Prohibit Key/Cert. with Weak Encryption] in [Encryption Settings] is set to [On], the hash algorithm SHA-1, which is used for signing a root certificate, can be used. |
TLS
The following combinations of the TLS version and algorithm are usable:
 : Usable
: Usable 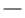 : Not usable
: Not usableAlgorithm | TLS Version | |||
TLS 1.3 | TLS 1.2 | TLS 1.1 | TLS 1.0 | |
Encryption Algorithm | ||||
AES-CBC (256bit) | 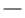 |  |  |  |
AES-CBC (128bit) | 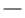 |  |  |  |
AES-GCM (256bit) |  |  | 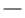 | 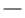 |
AES-GCM (128bit) |  |  | 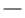 | 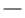 |
3DES-CBC | 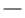 |  |  |  |
CHACHA20-POLY1305 |  | 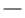 | 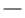 | 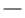 |
Key Exchange Algorithm | ||||
RSA | 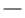 |  |  |  |
ECDHE |  |  |  |  |
X25519 |  | 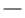 | 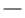 | 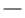 |
Signature Algorithm | ||||
RSA |  |  |  |  |
ECDSA |  |  |  |  |
HMAC Algorithm | ||||
SHA1 | 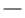 |  |  |  |
SHA256 |  |  | 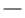 | 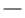 |
SHA384 |  |  | 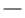 | 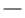 |