
Configuring the IPSec Settings
By using IPSec, you can prevent third parties from intercepting or tampering with IP packets transported over the IP network. Because IPSec adds security functions to IP, a basic protocol suite used for the Internet, it can provide security that is independent of applications or network configuration. To perform IPSec communication with this machine, you must configure settings such as the application parameters and the algorithm for authentication and encryption. Administrator privileges are required in order to configure these settings.
 |
Communication modeThis machine only supports transport mode for IPSec communication. As a result, authentication and encryption is only applied to the data portions of IP packets. Key exchange protocolThis machine supports Internet Key Exchange version 1 (IKEv1) for exchanging keys based on the Internet Security Association and Key Management Protocol (ISAKMP). For the authentication method, set either the pre-shared key method or the digital signature method. When setting the pre-shared key method, you need to decide on a passphrase (pre-shared key) in advance, which is used between the machine and the IPSec communication peer. When setting the digital signature method, use a CA certificate and a PKCS#12 format key and certificate to perform mutual authentication between the machine and the IPSec communication peer. For more information on registering new CA certificates or keys/certificates, see Registering a Key and Certificate for Network Communication. Note that SNTP must be configured for the machine before it uses this method. Making SNTP Settings |
 |
Regardless of the setting of [Format Encryption Method to FIPS 140-2] for IPSec communication, an encryption module which has already obtained FIPS140-2 certification will be used. In order to make IPSec communication comply with FIPS 140-2, you must set the key length of both DH and RSA for IPSec communication to 2048-bit or longer in the network environment that the machine belongs to. Only the key length for DH can be specified from the machine. Take note when configuring your environment, as there are no settings for RSA in the machine. You can register up to 10 security policies. |
Enabling IPSec
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Network Settings]  [IPSec Settings].
[IPSec Settings].
 [IPSec Settings].
[IPSec Settings].4
Select [Use IPSec], and click [OK].

To only receive packets that correspond to the security policy, select [Reject] for [Receive Non-Policy Packets].
Registering a Policy
1
Start the Remote UI. Starting the Remote UI
2
Click [Settings/Registration] on the portal page. Remote UI Screen
3
Click [Network Settings]  [IPSec Policy List].
[IPSec Policy List].
 [IPSec Policy List].
[IPSec Policy List].4
Click [Register New IPSec Policy].
5
Set a policy.
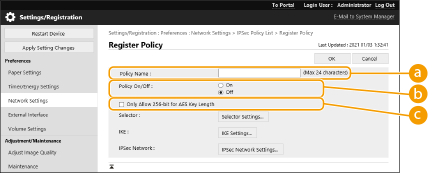
 [Policy Name]
[Policy Name]Enter a name for identifying the policy.
 [Policy On/Off]
[Policy On/Off]Select [On] to enable the registered policy.
 [Only Allow 256-bit for AES Key Length]
[Only Allow 256-bit for AES Key Length]Select this check box to restrict the key length of the AES encryption method to 256 bit and meet CC authentication standards.
6
Configure the IPSec application parameters.
1 | Click [Selector Settings]. | ||||||||||||||
2 | Specify the IP address to apply the IPSec policy to. Specify the IP address of this machine in [Local Address], and specify the IP address of the communication peer in [Remote Address]. 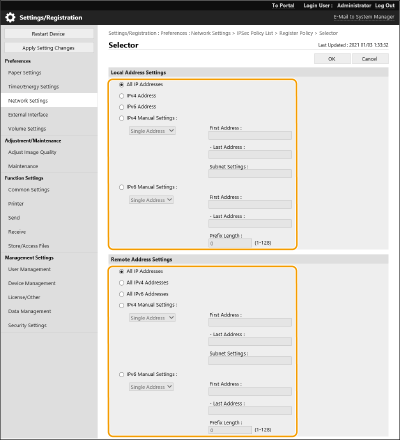
| ||||||||||||||
3 | Specify the port to apply IPSec to. 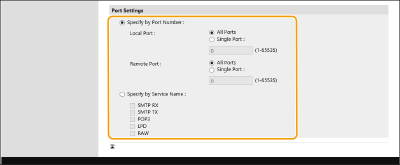 Select [Specify by Port Number] to use port numbers when specifying the ports that IPSec applies to. Select [All Ports] to apply IPSec to all port numbers. To apply IPSec to a specific port number [Single Port] and enter the port number. Specify the port of this machine in [Local Port], and specify the port of the communication peer in [Remote Port]. To specify the ports to apply IPSec to by service name, select [Specify by Service Name] and select the services to use. | ||||||||||||||
4 | Click [OK]. |
7
Configure the authentication and encryption settings.
1 | Click [IKE Settings]. | ||||||||||
2 | Configure the necessary settings. 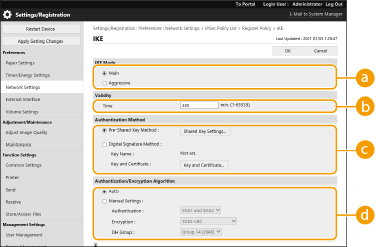  [IKE Mode] [IKE Mode]Select the operation mode for the key exchange protocol. Security is enhanced if you select [Main] because the IKE session itself is encrypted, but the speed of the session is slower than with [Aggressive], which does not encrypt the entire session.  [Validity] [Validity]Set the expiration period of the generated IKE SA.  [Authentication Method] [Authentication Method]Select one of the authentication methods described below.
 [Authentication/Encryption Algorithm] [Authentication/Encryption Algorithm]Select either [Auto] or [Manual Settings] to set how to specify the authentication and encryption algorithm for IKE phase 1. If you select [Auto] an algorithm that can be used by both this machine and the communication peer is set automatically. If you want to specify a particular algorithm, select [Manual Settings] and configure the settings below.
| ||||||||||
3 | Click [OK]. |
 |
When [IKE Mode] is set to [Main] on the [IKE] screen and [Authentication Method] is set to [Pre-Shared Key Method], the following restrictions apply when registering multiple security policies. Pre-shared key method key: when specifying multiple remote IP addresses to which a security policy is to be applied, all shared keys for that security policy are identical (this does not apply when a single address is specified). Priority: when specifying multiple remote IP addresses to which a security policy is to be applied, the priority of that security policy is below security policies for which a single address is specified. |
8
Configure the IPSec communication settings.
1 | Click [IPSec Network Settings]. | ||||||
2 | Configure the necessary settings. 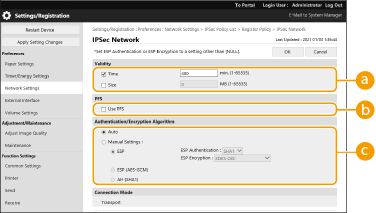  [Validity] [Validity]Set the expiration period of the generated IPSec SA. Make sure to set either [Time] or [Size]. If you set both, the setting with the value that is reached first is applied.  [PFS] [PFS]If you select [Use PFS], the secrecy of the encryption key is increased but communication speed is slower. In addition, the Perfect Forward Secrecy (PFS) function must be enabled on the communication peer device.  [Authentication/Encryption Algorithm] [Authentication/Encryption Algorithm]Select either [Auto] or [Manual Settings] to set how to specify the authentication and encryption algorithm for IKE phase 2. If you select [Auto], the ESP authentication and encryption algorithm is set automatically. If you want to specify a particular authentication method, select [Manual Settings] and select one of the authentication methods below.
| ||||||
3 | Click [OK] . |
9
Click [OK].
10
Enable the registered policies and check the order of priority.
Policies are applied in the order that they are listed, starting at the top. If you want to change the order of priority, select a policy in the list and click [Raise Priority] or [Lower Priority].
 |
Managing IPSec policiesYou can edit policies on the screen displayed in step 4. To edit the details of a policy, click the policy name in the list. To disable a policy, click the policy name in the list  select [Off] for [Policy On/Off] select [Off] for [Policy On/Off]  click [OK]. click [OK].To delete a policy, select the policy in the list  click [Delete] click [Delete]  [OK]. [OK].Using the control panelYou can also enable or disable IPSec communication from <Set> in the <Home> screen. <IPSec Settings> Batch importing/batch exportingThis setting can be imported/exported with models that support batch importing of this setting. Importing/Exporting the Setting Data This setting is included in [Settings/Registration Basic Information] when batch exporting. Importing/Exporting All Settings |