Security and Management Function Specifications
Authentication Functions
The following types of servers can be used as an external authentication server:
Windows Server with Active Directory installed
LDAP server
Cloud server using Microsoft Entra ID
Using Windows Server with Active Directory Installed
Software (Operating System)*1 | Windows Server 2016, 2019, 2022, 2025 *2 |
Kerberos Encryption Type*3 | AES (Advanced Encryption Standard) 128 bits AES (Advanced Encryption Standard) 256 bits DES (Data Encryption Standard) RC4 |
Port Number | Communication with DNS Server 53 Communication with Key Distribution Center (KDC) 88 Communication with LDAP Service 389 *4 |
*1When Kerberos Armoring is enabled with a policy related to KDC (group policy), the user can no longer log in with Active Directory authentication. Disable Kerberos Armoring to use this software.
*2LDAP/LDAPS communication is not possible with the default setting of Windows Server. Install a server certificate on Windows Server and communicate with LDAPS (TLS).
*3The available encryption type varies depending on the Active Directory setting. In addition, a high level encryption type is selected automatically from among the available encryption types.
*4This is the default port number. The port number may vary if the LDAP service setting has been changed.
When Using an LDAP Server
Software | OpenLDAP |
Operating System | Conforms the specifications of the LDAP server |
Port Number*1 | When Using TLS 636 When Not Using TLS 389 |
*1This is the default port number. You can change the port number according to the LDAP server settings.
Default Settings for the Firewall of the Sub Line
By default, the outbound and inbound filters of the IP address are set for the sub line. Therefore, by default, only the following exception addresses and exception port numbers are available for communication on the sub line.
Default Policy | Reject |
Exception Addresses | 0.0.0.1 to 255.255.255.255 |
Exception Port Numbers | 53, 67, 68, 80, 161, 443, 515 *1, 631 *1, 3702, 5353, 5357, 5358, 8000 *1, 8080, 8443 *1, 9013, 9100 *1, 10443 *1, 20010 *1, 47545 |
*1Inbound filter only.
TLS
The combinations of TLS versions and algorithms that can be used with the machine are shown below.
 : Usable
: Usable 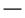 : Not usable
: Not usableAlgorithm | TLS Version | |||
TLS 1.3 | TLS 1.2 | TLS 1.1 | TLS 1.0 | |
Encryption Algorithm | ||||
AES-CBC (256 bits) | 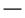 |  |  |  |
AES-GCM (256 bits) |  |  | 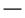 | 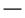 |
3DES-CBC | 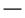 |  |  |  |
AES-CBC (128 bits) | 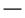 |  |  |  |
AES-GCM (128 bits) |  |  | 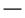 | 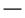 |
CHACHA20-POLY1305 |  | 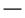 | 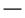 | 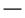 |
Key Exchange Algorithm | ||||
RSA | 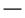 |  |  |  |
ECDHE |  |  |  |  |
X25519 |  | 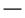 | 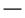 | 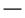 |
Signature Algorithm | ||||
RSA |  |  |  |  |
ECDSA |  |  |  |  |
HMAC Algorithm | ||||
SHA1x | 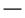 |  |  |  |
SHA256 |  |  | 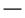 | 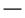 |
SHA384 |  |  | 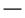 | 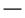 |
IPSec
IPSec of the machine conforms to RFC2407, RFC2408, RFC2409, RFC4109, RFC4301, RFC4302, RFC4303, and RFC4305.
Operating system of connected device | Windows 10, 11 Windows Server 2016, 2019, 2022, 2025 |
Connection mode | Transport mode |
Key exchange protocol | IKEv1 (main mode and aggressive mode) |
Authentication Method Pre-shared key Digital signature | |
Hash Algorithm (and Key Length) HMAC-SHA1-96 HMAC-SHA2 (256 bits or 384 bits) | |
Encryption Algorithm (and Key Length) 3DES-CBC AES-CBC (128 bits, 192 bits, 256 bits) | |
Key Exchange Algorithm/Group (and Key Length) Diffie-Hellman (DH) Group 14 (2048 bits) ECDH-P256 ECDH-P384 | |
ESP | Hash Algorithm HMAC-SHA1-96 |
Encryption Algorithm (and Key Length) 3DES-CBC AES-CBC (128 bits, 192 bits, 256 bits) | |
Hash/Encryption Algorithm (and Key Length) AES-GCM (128 bits, 192 bits, 256 bits) | |
AH | Hash Algorithm HMAC-SHA1-96 |
NOTE
IPSec supports communication to a unicast address (single device).
Keys and Certificates
Self-generated Key and Self-signed Certificate, and CSR
Public Key Algorithm (and Key Length) | RSA (512 bits, 1024 bits, 2048 bits, 4096 bits) ECDSA (P256, P384, P521) |
Certificate Signature Algorithm | RSA SHA-256, SHA-384 *1, SHA-512 *1 ECDSA SHA-256, SHA-384, SHA-512 |
*1Available only when the key length is 1024 bits or more.
Key and Certificate, CA Certificate, or S/MIME Certificate for Installation
Type | Key and Certificate*1 PKCS#12 Key and Certificate for User Signature PKCS#12 CA Certificate and S/MIME Certificate X.509 DER or PEM format |
File extension | Key and Certificate*1 ".p12" or ".pfx" Key and Certificate for User Signature ".p12" or ".pfx" CA Certificate and S/MIME Certificate ".cer" or ".pem" |
Public key algorithm (and key length) | RSA (512 bits*2, 1024 bits, 2048 bits, 4096 bits*2) DSA (1024 bits, 2048 bits, 3072 bits)*2 ECDSA (P256, P384, P521) |
Certificate signature algorithm | RSA SHA-1, SHA-256, SHA-384 *3, SHA-512 *3, MD2 *2, MD5 *2 DSA SHA-1 *2 ECDSA SHA-1 *2, SHA-256, SHA-384, SHA-512 |
*1Used for TLS, IEEE 802.1X, IPSec, and device signature.
*2Cannot be used for user signature.
*3Available only when the key length is 1024 bits or more.
Number of Keys and Certificates That Can Be Registered
Number of Keys and Certificates That Can Be Registered | Key and Certificate*1 6 Key and Certificate for User Signature For 100 people (one per user) CA Certificate 150 S/MIME Certificate 2,000 |
*1Used for TLS, IEEE 802.1X, IPSec, and device signature.
Registering a Certificate Revocation List (CRL)
You can register up to 50 certificate revocation lists (CRL). However, a CRL cannot be registered in the following cases:
When the size of the CRL exceeds 1 MB
When using a signature algorithm that is not supported
When the number of revoked certificates registered to a CRL exceeds 10,000
Definition of "Weak Encryption"
When [Prohibit Use of Weak Encryption] is set to [On], the use of the following algorithms is prohibited. [Prohibit Use of Weak Encryption]
Hash | MD4, MD5, SHA-1 |
HMAC | HMAC-MD5 |
Common Key Encryption | RC2, RC4, DES |
Public Key Encryption | RSA encryption (512 bits, 1024 bits) RSA signature (512 bits, 1024 bits) DSA (512 bits, 1024 bits) DH (512 bits, 1024 bits) |
NOTE
Even when [Prohibit Use of Key/Certificate with Weak Encryption] is set to [On], the hash algorithm SHA-1, which is used for signing a root certificate, can be used.
Algorithm Compliant with FIPS140
When [Format Encryption Method to FIPS 140] is set to [On], the use of the following algorithms is prohibited. [Format Encryption Method to FIPS 140]
Hash | MD2, MD4, MD5, SHA-1 (applications other than TLS) |
Common key encryption | RC2, RC4, RC5, DES, ChaCha20-Poly1305, 3DES |
Public key encryption | RSA encryption (512 bits, 1024 bits) RSA signature (512 bits, 1024 bits) DSA signature (512 bits, 1024 bits) DH (512 bits, 1024 bits) X25519 |
Log Type
You can manage the logs below on the machine. You can also export a collected log to a CSV file.
Log type | Number of log types listed in CSV file | Overview |
User Authentication Log | 4098 | Log related to authentication status (login/logout, authentication success/fail) for User Authentication, registration, change, and deletion of user information managed by User Authentication, and role management (add, set, delete) of Access Management System. |
Job Log | 1001 | Log that keeps track of print, scan, fax, and copy jobs. |
Transmission Log | 8193 | Log that keeps track of sending and receiving. |
Advanced Space Save Log | 8196 | Log related to Advanced Space, network (Advanced Space on other devices), and storage of files to memory media. |
Box Operation Log | 8197 | Log related to the data operations of Mail Box, Memory RX Inbox, and Confidential Fax Inbox. |
Box Authentication Log | 8199 | Log related to the authentication status of Mail Box, Memory RX Inbox, and Confidential Fax Inbox. |
Advanced Space Operation Log | 8201 | Log related to the operations using data in Advanced Space. |
Machine Management Log | 8198 | Log related to ON/OFF operations of the machine, setting changes using [  Settings/Registration], setting changes via device information distribution, and other information. Settings/Registration], setting changes via device information distribution, and other information. Changes to settings related to user information or security performed during inspection or repair by your dealer or service representative are also recorded in the machine management log. |
Network Authentication Log | 8200 | Log recorded when IPSec Network communication fails. |
Import/Export All Log | 8202 | Log related to the batch import and export of settings. |
Box Backup Log | 8203 | Log that keeps track of the backup of the following data: Mail Box data Memory RX Inbox data Confidential Fax Inbox data Advanced Space data Hold Queue data (for C7100 Series and C5100 Series) Registration of form for Superimpose Image (for C7100 Series and C5100 Series) |
Operation Log of Application and Software Management Screen | 3101 | Log related to the operations of Service Management Service (SMS), Register/Update Software, MEAP Application installer, and other services. |
Security Policy Log | 8204 | Log related to Security Policy setting status. |
Group Management Log | 8205 | Log related to the user group setting status (registration, change, deletion). |
System Maintenance Log | 8206 | Log related to firmware updates, MEAP Application backups and recovery, and other operations. |
Authentication Print Log | 8207 | Log related to information of jobs being held and operation history. |
Settings Synchronization Log | 8208 | Log related to synchronizing personalized data. Using Multiple Canon Multifunction Machines with the Same Settings (Synchronizing Personalized Data) |
Log for Audit Log Management | 3001 | Log related to starting and ending log recording, exporting logs, and other operations. |
NOTE
You can record up to 40,000 logs. When the number of logs exceeds 40,000, new logs replace the oldest log in chronological order.
External Storage for Backup and Recovery
Interface | USB 2.0, USB 3.0 |
File System | FAT32, exFAT |
Partition Size | Larger than 32 GB (not separated into multiple partitions) |
Power Supply | Supplied from an external power source |
Visual Message
File Format | JPEG, PNG, BMP, GIF, animated GIF, HTML (in intranet, Internet) |
File Size | Up to 10 MB |
Content Display Size | 799 pixels x 509 pixels JPEG, PNG, BMP, GIF, animated GIF When the size exceeds the above specifications, the content size is reduced while the aspect ratio is maintained. When the size is smaller than the above specifications, the content is displayed at the original size without being enlarged. HTML When the size exceeds the above specifications, the content is displayed at the original size without being reduced (scrolling is supported). When the size is smaller than the above specifications, the content is displayed at the original size without being enlarged. |
Communication Protocols | SMB, WebDAV, HTTP |