Registering Authentication Server Information
When using an Active Directory, LDAP server, or Microsoft Entra ID as an external authentication server, register the information of the server to be used.
Register the server information using Remote UI from a computer. You cannot use the control panel to register the information.
Administrator privileges are required. The machine must be restarted to apply the registered information.
Administrator privileges are required. The machine must be restarted to apply the registered information.
Required Preparations
You must configure the settings required to use an Active Directory, LDAP server, or Microsoft Entra ID, such as the DNS settings and the date and time settings.
Prepare the credentials for accessing the Active Directory, LDAP server, or Microsoft Entra ID you want to use.
1
Log in to Remote UI as an administrator. Starting Remote UI
2
On the Portal page of Remote UI, click [Settings/Registration]. Remote UI Portal Page
3
Click [User Management]  [Authentication Management]
[Authentication Management]  [Server Settings]
[Server Settings]  [Edit].
[Edit].
 [Authentication Management]
[Authentication Management]  [Server Settings]
[Server Settings]  [Edit].
[Edit].The [Edit Server Settings] screen is displayed.
4
Configure the Active Directory, LDAP server, or Microsoft Entra ID information in [Authentication Server].
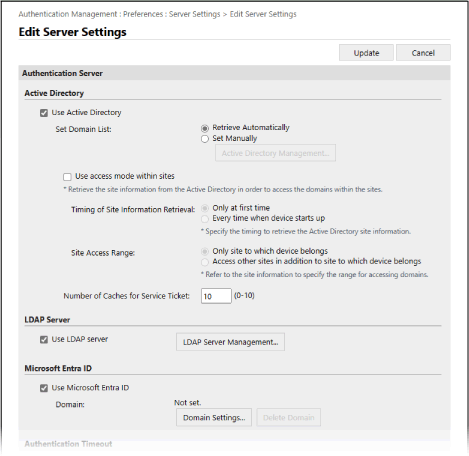
When Obtaining the Active Directory Information Automatically

1
Select the [Use Active Directory] checkbox.
2
In [Set Domain List], select [Retrieve Automatically].
3
Specify the method for accessing Active Directory and the number of caches.
[Use access mode within sites]
When using multiple Active Directory servers, select this checkbox to assign access priority to the Active Directory within the site to which the machine belongs.
Change the settings for [Timing of Site Information Retrieval] and [Site Access Range], as needed.
Change the settings for [Timing of Site Information Retrieval] and [Site Access Range], as needed.
* Even when [Only site to which device belongs] in [Site Access Range] is specified, the machine may access sites outside the site to which it belongs when performing domain controller access during the startup process. In this case, access to domain controllers within the same site is usually given priority.
However, if domain controllers within the same site cannot be accessed but domain controllers outside the site can be accessed, priority is given to accessing domain controllers outside the site.
[Number of Caches for Service Ticket]
Specify the number of service tickets that the machine can hold.
A service ticket is an Active Directory function that acts as a record of a previous login, which reduces the amount of time it takes for the same user to log in next time.
A service ticket is an Active Directory function that acts as a record of a previous login, which reduces the amount of time it takes for the same user to log in next time.
Specifying the Active Directory Information Manually

1
Select the [Use Active Directory] checkbox.
2
In [Set Domain List], select [Set Manually].
3
Click [Active Directory Management]  [OK].
[OK].
 [OK].
[OK].The [Active Directory Management] screen is displayed.
4
Click [Add Domain].
The [Add Domain] screen is displayed.
5
Specify the Active Directory information.
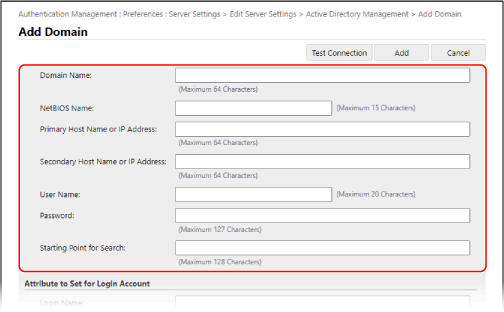
[Domain Name]
Enter the domain name of Active Directory that is the login destination.
Input example:
company.domain.com
company.domain.com
[NetBIOS Name]
Enter the NetBIOS domain name.
[Primary Host Name or IP Address] / [Secondary Host Name or IP Address]
Enter the host name or IP address of the Active Directory server.
* To use a secondary server, specify the server in [Secondary Host Name or IP Address].
[User Name] and [Password]
Enter the user name and password to use for accessing the Active Directory server and searching for user information.
[Position to Start Search]
Specify the location (level) to search for user information when Active Directory server authentication is performed. If you do not specify the search start position, all user information registered on the server will be searched.
6
Specify the attributes.
[Attribute to Set for Login Account]
Enter the attributes for the login name, display name, and e-mail address of each user account on the server.
7
Click [Connection Test] to test the connection.
8
Click [Add].
The server information is added and the [Active Directory Management] screen is displayed again.
9
Click [Back].
The [Edit Server Settings] screen is displayed again.
10
Specify the number of caches in [Number of Caches for Service Ticket].
Specify the number of service tickets that the machine can hold.
A service ticket is an Active Directory function that acts as a record of a previous login, which reduces the amount of time it takes for the same user to log in next time.
A service ticket is an Active Directory function that acts as a record of a previous login, which reduces the amount of time it takes for the same user to log in next time.
Specifying the LDAP Server Information

1
Select the [Use LDAP server] checkbox.
2
Click [LDAP Server Management]  [OK].
[OK].
 [OK].
[OK].The [LDAP Server Management] screen is displayed.
3
Click [Add Server].
The [Add LDAP Server] screen is displayed.
4
Specify the LDAP server information.
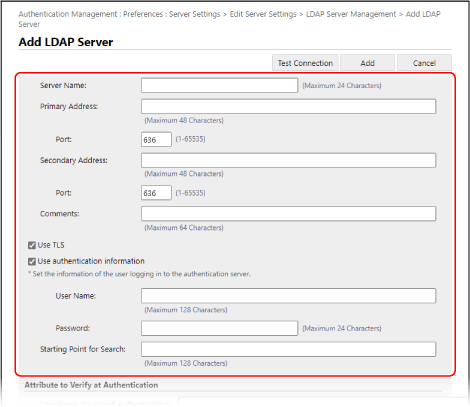
[Server Name]
Enter the name used to identify the LDAP server.
* Do not use the name "localhost." Do not include spaces in the server name.
[Primary Address] and [Secondary Address]
Enter the IP address or host name of the LDAP server.
Input example: Host name
ldap.example.com
ldap.example.com
* Do not use a loopback address (127.0.0.1).
* When using a secondary server, enter the IP address or host name in [Secondary Address].
[Port]
Enter the port number used for communicating with the LDAP server.
* If left blank, the following setting is used according to the [Use TLS] setting:
When the checkbox is selected, "636"
When the checkbox is cleared, "389"
[Comments]
Enter a description and notes, as needed.
[Use TLS]
Select this checkbox when using TLS encryption for communication with the LDAP server.
[Use authentication information]
When using authentication information for LDAP server authentication, select the checkbox and enter the user name and password for authentication.
Clear the checkbox to allow anonymous access to the LDAP server without using authentication information.
* Only when the LDAP server is set to allow anonymous access.
[Starting Point for Search]
Specify the location (level) to search for user information when LDAP server authentication is performed.
5
Specify the attributes.
[Attribute to Verify at Authentication]
Enter the attributes to which the user name is registered in [User Name (Keyboard Authentication)].
[Attribute to Set for Login Account]
Enter the attributes for the login name, display name, and e-mail address of each user account on the server.
6
Specify the domain name of the login destination in [Domain Name Setting Method].
To specify the attribute to which the domain name is registered, select [Specify the attribute name for domain name acquisition] and enter the attribute.
7
Click [Connection Test] to test the connection.
8
Click [Add].
The server information is added and the [LDAP Server Management] screen is displayed again.
9
Click [Back].
The [Edit Server Settings] screen is displayed again.
Specifying the Microsoft Entra ID Information

1
Select the [Use Microsoft Entra ID] checkbox.
2
Click [Domain Settings].
The [Microsoft Entra ID Domain Settings] screen is displayed.
3
Specify the Microsoft Entra ID information.
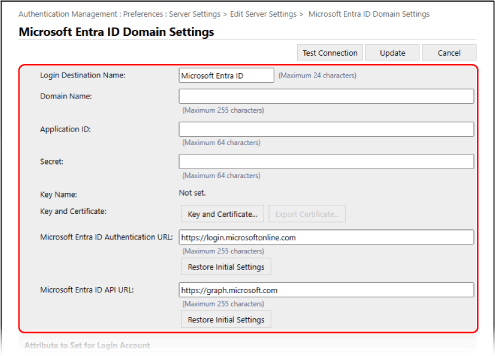
[Login Destination Name]
Enter the name to be displayed at the login destination.
[Domain Name]
Enter the domain name of the Microsoft Entra ID that is the login destination.
[Application ID]
Enter the application (client) ID.
[Secret]
Enter the secret generated by Microsoft Entra ID. You do not need to enter this when [Key and Certificate] is used.
[Key and Certificate]
Click [Key and Certificate] to set the certificate to be registered to Microsoft Entra ID when you use a key and certificate. Select the certificate for which the key algorithm is RSA 2048 bits or more and the signature algorithm is SHA256, SHA384, or SHA512.
You can click [Export Certificate] to export the certificate to be registered to Microsoft Entra ID.
You can click [Export Certificate] to export the certificate to be registered to Microsoft Entra ID.
[Use Microsoft Login Screen]
Select this checkbox to display the Microsoft login screen for logging in with multi-factor authentication, when Microsoft Entra ID multi-factor authentication is enabled.
* [Browser Engine] in [Web Access] is required to be set to [WebKit2]. [Web Access]
* When [Auto Reset Time] is set to [10] seconds, the Auto Reset function may be performed before the login screen is displayed. In this case, change the Auto Reset time. [Auto Reset Time]
[Microsoft Entra ID Authentication URL] and [Microsoft Entra ID API URL]
Enter the URLs. Depending on your cloud environment, you may need to change the settings. You do not need to enter this when [Secret] is used.
4
Specify the attributes.
[Attribute to Set for Login Account]
[Login Name]
From the pulldown menu, select the attribute for the login name of each user account on the server.
* To specify an attribute not displayed in the pulldown menu, you can enter it directly.
[WindowsLogonName]:
displayName is obtained from Microsoft Entra ID. displayName is changed as follows to create the login name:
displayName is obtained from Microsoft Entra ID. displayName is changed as follows to create the login name:
Spaces and the following characters are deleted from displayName: * + , . / : ; < > = ? \ [ ] |.
"@" and any subsequent characters are deleted.
Character strings exceeding 20 characters are shortened to 20 characters or less.
Example: When displayName is user.001@example.com
user001
user001
[displayName]:
displayName obtained from Microsoft Entra ID becomes the login name.
displayName obtained from Microsoft Entra ID becomes the login name.
[userPrincipalName]:
userPrincipalName obtained from Microsoft Entra ID becomes the login name.
userPrincipalName obtained from Microsoft Entra ID becomes the login name.
[userPrincipalName-Prefix]:
The portion before "@" in userPrincipalName obtained from Microsoft Entra ID becomes the login name.
Example: When userPrincipalName is "user.002@mail.test"
user.002
The portion before "@" in userPrincipalName obtained from Microsoft Entra ID becomes the login name.
Example: When userPrincipalName is "user.002@mail.test"
user.002
[Display Name] and [E-Mail Address]
Enter the attributes for the display name and e-mail address of each user account on the server.
5
Specify the domain name of the login destination in [Domain Name] under [Domain Name to Set for Login Account].
6
Specify the settings in [Autocomplete for Entering User Name When Using Keyboard Authentication] under [Domain Name to Autocomplete].
Enter the name of the domain for which to perform autocomplete. Normally, set the same name as entered in [Domain Name].
7
Click [Connection Test] to test the connection.
8
Click [Update].
The [Edit Server Settings] screen is displayed again.
Enter the time from start of authentication to timeout in [Authentication Timeout].
6
Specify the priority domain to which to connect in [Default Domain].
Specify whether to retain the authentication information of users in [Cache for User Information].
To retain the authentication information of users who logged in with the control panel, select the [Save authentication information for login users] checkbox. If the machine is unable to connect to the authentication server within the time set in Step 5, you can log in using the authentication information held in the cache.
To retain the authentication information of users who logged in with keyboard authentication, also select the [Save user information when using keyboard authentication] checkbox.
When this checkbox is selected, even if the machine is unable to connect to the server, you can log in using the held authentication information.
When this checkbox is selected, even if the machine is unable to connect to the server, you can log in using the held authentication information.
8
Specify the user information and privileges in [Role Association].
[User Attribute to Browse]
Enter the attribute on the referenced server that is used to determine user privileges (roles). Normally, you can use the preset value of "memberOf," which indicates the group to which the user belongs.
[Retrieve role name to apply from [User Attribute to Browse]]
Select this checkbox to use the character string registered to the attribute specified in [User Attribute to Browse] for the role name. Before selecting the checkbox, check the role names that can be selected on the machine and register them on the server.
[Conditions]
You can set the conditions to determine user privileges. The conditions are applied in the order they are listed.
In [Search Criteria], select the search criteria for [Character String].
In [Character String], enter the character string registered to the attribute specified in [User Attribute to Browse]. To specify the privileges based on the group to which the user belongs, enter the group name.
In [Role], select the privileges that apply to users who match the criteria.
* When using an Active Directory server, users who belong to the "Canon Peripheral Admins" group are set in advance to [Administrator].
9
Click [Update].
10
Restart the machine. Restarting the Machine
The information is registered.
NOTE
Prohibiting Cache Storage of Authentication Information
You can prohibit cache storage of passwords that users enter at login to the external authentication server. [Prohibit Caching of Authentication Password]
When cache storage is prohibited, the [Save authentication information for login users] setting in Step 7 is disabled automatically. To enable the setting in Step 7, select the [Save authentication information for login users] checkbox and update the authentication server information.
If the Port Number for Kerberos on Active Directory Is Changed
Register the following information to the DNS server as an SRV record:
Service: "_kerberos"
Protocol: "_udp"
Port number: Port number actually used by the Kerberos service of the Active Directory domain (zone)
Host offering this service: Host name of the domain controller that is actually providing the Kerberos service of the Active Directory domain (zone)
Registering an Application in Microsoft Entra ID
Use the following procedure to register an application in Microsoft Entra ID.
The registration process may change with service updates. For more information, see the Microsoft website.
The registration process may change with service updates. For more information, see the Microsoft website.
1
Log in to Microsoft Entra ID.
2
In the navigation menu, click [Microsoft Entra ID].
3
Register the application.
1
In the navigation menu, click [App registrations]  [New registration].
[New registration].
 [New registration].
[New registration].2
Enter the name of the application.
You can enter any name.
Input example:
Canon <printer name> Login
Input example:
Canon <printer name> Login
3
Select the type of account, and click [Register].
The application (client) ID is generated.
Make a note of the generated ID.
Make a note of the generated ID.
4
Create a secret or register a certificate.
When Creating a Secret

1
In the navigation menu, click [Certificates & secrets].
2
Click [New Scanclient secret].
3
In the [Add a client secret] dialog box, enter the description and expiry date, and click [Add].
A secret ID and value are created.
Make a note of the created secret value. You do not need the secret ID.
* The secret value is only displayed once. If you are unable to make a note of the value, create a new client secret.
Make a note of the created secret value. You do not need the secret ID.
* The secret value is only displayed once. If you are unable to make a note of the value, create a new client secret.
When Registering a Certificate

The certificate of the machine needs to be exported in advance. You can export the certificate when configuring the Microsoft Entra ID information. Registering Authentication Server Information
1
In the navigation menu, click [Certificates & secrets].
2
Click [Upload certificate].
3
Select the file, and click [Add].
After the certificate is uploaded, make a note of the [Thumbprint] value.
5
In the navigation menu, click [API permissions].
6
Click [Add a permissions].
7
Under [Request API permissions], select [Microsoft Graph].
8
Under the type of permissions, select [Delegated permissions], and grant permissions.
Grant the following permissions:
User.Read.All
Group.Read.All
GroupMember.Read.All
9
Under the type of permissions, select [Application permissions], and grant permissions.
Grant the following permissions:
User.Read.All
Group.Read.All
GroupMember.Read.All
* Use permissions when you cannot log in to the machine due to a multifactor authentication error. This is not required depending on the function and environment used.
10
Click [Grant admin consent confirmation], and click [Yes].
Admin consent is granted to the selected permissions.