Using TLS
Transport Layer Security (TLS) is a mechanism for encrypting data sent and received over the network. Encrypting communication with TLS when using Remote UI reduces the risks of data eavesdropping and tampering during communication.
To use TLS, configure the TLS settings and enable TLS for each function.
To use TLS, configure the TLS settings and enable TLS for each function.
Step 1: Configuring the TLS Settings
Specify the key and certificate (server certificate) that you want to use with TLS encrypted communication, and then specify the versions and algorithms for TLS.
This section describes how to configure the settings using Remote UI from a computer.
On the control panel, select [ Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [TLS Settings]
Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [TLS Settings]
Administrator or NetworkAdmin privileges are required. The machine must be restarted to apply the settings.
On the control panel, select [
 Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [TLS Settings]
Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [TLS Settings]Administrator or NetworkAdmin privileges are required. The machine must be restarted to apply the settings.
Required Preparations
Prepare the key and certificate to use for TLS encrypted communication. Managing and Verifying a Key and Certificate
* You can also use the key and certificate already registered in the machine.
1
Log in to Remote UI as an administrator. Starting Remote UI
2
On the Portal page of Remote UI, click [Settings/Registration]. Remote UI Portal Page
3
Click [Network Settings]  [TLS Settings].
[TLS Settings].
 [TLS Settings].
[TLS Settings].The [TLS Settings] screen is displayed.
4
Specify the key and certificate to use for TLS encrypted communication.
1
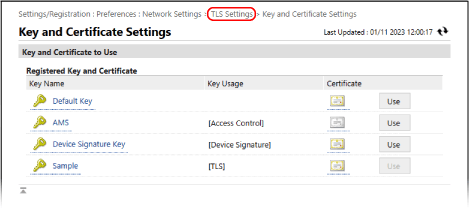
In [Key and Certificate Settings], click [Key and Certificate].
The [Key and Certificate Settings] screen is displayed.
2
Click [Use] to the right of the key and certificate to use.
Click the key name (or certificate icon) to display the certificate details.
On the certificate details screen, click [Verify Certificate] to verify that the certificate is valid.
To use the key and certificate already registered in the machine, select "Default Key."
* TLS encrypted communication cannot be used with the following keys and certificates:
AMS (for access restriction)
Device Signature Key (for device signature)
5
Click [TLS Settings] at the top of the Remote UI screen.
The [TLS Settings] screen is displayed again.
6
Specify the versions and algorithms for TLS.
Some combinations of versions and algorithms cannot be used. For the supported combinations of versions and algorithms, see the TLS specifications. TLS
[Specify Allowed Versions]
Select the maximum and minimum versionsof TLS.
[Algorithm Settings]
Select the checkbox of the algorithm to use for TLS.
7
Click [OK].
8
Restart the machine. Restarting the Machine
The settings are applied.
NOTE
Conforming the Encryption Method to FIPS 140
You can conform the encryption method of TLS encryption communication to FIPS 140. Algorithm Compliant with FIPS140
When the encryption method conforms to FIPS 140, the TLS settings and communications are restricted as follows.
If you try to specify a certificate that uses an algorithm not recognized by FIPS (RSA keys with less than 2048 bits) for TLS, an error will occur.
A communication error will occur with parties that do not support FIPS-recognized encryption algorithms.
The algorithms used for TLS, [CHACHA20-POLY1305] and [X25519], are disabled.
Step 2: Enabling TLS for Each Function
Specify the TLS settings, and then enable TLS encrypted communication for each function that can use TLS.
Remote UI [Remote UI]
LDAP server Registering LDAP Servers
IPP printing Setting the IPP Printing Function of the Machine
E-mail and I-Fax Configuring Information of the E-mail Server
Opening Advanced Space as a WebDAV server Preparations for Using Advanced Space
IEEE 802.1X authentication Using IEEE 802.1X
MEAP [Use TLS]
Network Link Scan [Use Network Link Scan]
Syslog sending Sending the Logs to the SIEM System
IP FAX
For details, see the manual of IP FAX Expansion Kit at the online manual site.
For details, see the manual of IP FAX Expansion Kit at the online manual site.
NOTE
When a Warning Message Appears at Remote UI Startup
A warning message about the security certificate may appear when starting up Remote UI with TLS enabled. If there are no problems with the certificate or TLS settings, you can continue operations.