Using IEEE 802.1X
In a network environment with IEEE 802.1X authentication, only client devices (supplicants) authenticated by the authentication server (RADIUS server) are allowed to connect to the network via the LAN switch (authenticator), thereby blocking unauthorized access. To connect the machine to a network that uses IEEE 802.1X authentication, you must configure the settings on the machine such as the authentication method managed by the authentication server.
* When the machine is connected to two different networks at the same time, you can use IEEE 802.1X on either the main line or the sub line. You can change these settings, as needed. You cannot use IEEE 802.1X on the main line and sub line at the same time.
IEEE 802.1X Authentication Methods
The following IEEE 802.1X authentication methods are supported:
TLS
The machine and authentication server authenticate each other by mutually verifying their certificates. This cannot be used together with another authentication method.
TTLS
This authentication method uses a user name and password for machine authentication and a CA certificate for the server authentication. MSCHAPv2 or PAP can be selected as the internal protocol, and TTLS can be used together with PEAP.
PEAP
The required settings are almost the same as those for TTLS, with MSCHAPv2 used as the internal protocol.
Configuring the IEEE 802.1X Settings
First enable IEEE 802.1X, and then set the authentication method.
This section describes how to configure the settings using Remote UI from a computer.
On the control panel, select [ Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [IEEE 802.1X Settings]
Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [IEEE 802.1X Settings]
Administrator or NetworkAdmin privileges are required. The machine must be restarted to apply the sub line settings.
On the control panel, select [
 Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [IEEE 802.1X Settings]
Settings/Registration] in the [Home] screen or other screen, and then select [Preferences] to configure the settings. [IEEE 802.1X Settings]Administrator or NetworkAdmin privileges are required. The machine must be restarted to apply the sub line settings.
Required Preparations
When using TLS as the authentication method, prepare the key and certificate issued by the certificate authority and used for authentication of the machine. Managing and Verifying a Key and Certificate
* A preinstalled CA certificate or a CA certificate installed from Remote UI is used for server authentication.
When using TTLS or PEAP as the authentication method, use TLS to encrypt communication using Remote UI. Using TLS
1
Log in to Remote UI as an administrator. Starting Remote UI
2
On the Portal page of Remote UI, click [Settings/Registration]. Remote UI Portal Page
3
Click [Network Settings]  [IEEE 802.1X Settings].
[IEEE 802.1X Settings].
 [IEEE 802.1X Settings].
[IEEE 802.1X Settings].The [IEEE 802.1X Settings] screen is displayed.
When Changing the Sub Line Settings
Click [Network Settings]  [IEEE 802.1X Settings] under [Sub Line Settings].
[IEEE 802.1X Settings] under [Sub Line Settings].
 [IEEE 802.1X Settings] under [Sub Line Settings].
[IEEE 802.1X Settings] under [Sub Line Settings].4
Select the [Use IEEE 802.1X] checkbox, and enter the login name.
For the login name, enter a name to identify the user (EAP Identity) using alphanumeric characters.
* When you select the [Use IEEE 802.1X] checkbox for either the main line or sub line, you cannot select the checkbox for the other line.
When Verifying the Certificate of an Authentication Server
Select the [Verify Authentication Server Certificate] checkbox.
To verify the Common Name of the certificate, select the [Verify Authentication Server Name] checkbox, and enter the name of the authentication server to which the user is registered.
To verify the Common Name of the certificate, select the [Verify Authentication Server Name] checkbox, and enter the name of the authentication server to which the user is registered.
5
Configure the settings according to the authentication method to be used.
When Using TLS

1
Select the [Use TLS] checkbox.
2
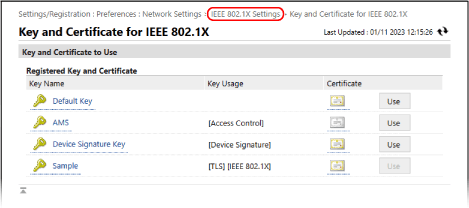
Click [Key and Certificate].
The [Key and Certificate for IEEE 802.1X] screen is displayed.
3
Click [Use] to the right of the key and certificate to use.
Click the key name (or certificate icon) to display the certificate details.
On the certificate details screen, click [Verify Certificate] to verify that the certificate is valid.
4
Click [IEEE 802.1X Settings] at the top of the Remote UI screen.
The [IEEE 802.1X Settings] screen is displayed again.
When Using TTLS or PEAP

1
Select the [Use TTLS] or [Use PEAP] checkbox.
When using TTLS, select the internal protocol to be used.
2
Use [Use Login Name as User Name] to specify whether to use the login name of IEEE 802.1X authentication for the user name.
3
Click [Change User Name/Password].
The [User Name/Password Settings] screen is displayed.
4
Set the user name and password.
Enter the user name using alphanumeric characters.
To set a password, enter the same password in both [Password] and [Confirm].
5
Click [OK].
The [IEEE 802.1X Settings] screen is displayed again.
6
Click [OK].
7
Click [Apply Setting Changes]  [OK].
[OK].
 [OK].
[OK].The settings are applied.
If you change the sub line settings, click [Apply Setting Changes] [Restart].
[Restart].
In [Basic Functions Status], check that there are no functions operating, and then click [Perform Restart].
If you change the sub line settings, click [Apply Setting Changes]
 [Restart].
[Restart].In [Basic Functions Status], check that there are no functions operating, and then click [Perform Restart].
8
Log out from Remote UI.